|
Introduction: In the fast-evolving landscape of technology, Artificial Intelligence (AI) has emerged as a transformative force. From enhancing efficiency to revolutionizing industries, AI is reshaping the way we live and work.
What is Artificial Intelligence? AI refers to the development of computer systems that can perform tasks that typically require human intelligence. These tasks include learning, reasoning, problem-solving, perception, speech recognition, and language translation. Key Components of AI:
0 Comments
As we enter the Holiday season, it's crucial to stay vigilant, as this period often sees a surge in phishing and spear-phishing attempts. With increased online shopping and a higher volume of emails, there's a heightened risk of falling victim to cyber threats.
Currently, there is an active phishing campaign targeting organizations in the UK, spanning various sectors, including academia, defense, governmental organizations, NGOs, think tanks, and politicians. It's important to note that these phishing emails may be directed to both personal and corporate email addresses. Spear-phishing emails are designed to appear as if they're from someone you know or trust. We urge you to exercise caution and think twice before clicking on any links or opening attachments in emails. A helpful tip is to hover over a link without clicking to reveal the actual website it leads to. Best Regards, Your Security Team Today, the Cybersecurity and Infrastructure Security Agency (CISA) released a joint Cybersecurity Advisory (CSA) Russian FSB Cyber Actor Star Blizzard Continues Worldwide Spear-phishing Campaigns. The joint CSA aims to raise awareness of the specific tactics, techniques, and delivery methods used by this Russia-based threat actor group to target individuals and organizations. Known Star Blizzard techniques include:
CDC alerts. Cybercriminals have sent phishing emails designed to look like they’re from the U.S. Centers for Disease Control. The email might falsely claim to link to a list of coronavirus cases in your area. “You are immediately advised to go through the cases above for safety hazard,” the text of one phishing email reads.
Health advice emails. Phishers have sent emails that offer purported medical advice to help protect you against the coronavirus. The emails might claim to be from medical experts near Wuhan, China, where the coronavirus outbreak began. “This little measure can save you,” one phishing email says. “Use the link below to download Safety Measures.” How do I help avoid scammers and fake ads?Scammers have posted ads that claim to offer treatment or cures for the coronavirus. The ads often try to create a sense of urgency — for instance, “Buy now, limited supply.” At least two bad things could happen if you respond to the ads. One, you might click on an ad and download malware onto your device. Two, you might buy the product and receive something useless, or nothing at all. Meanwhile, you may have shared personal information such as your name, address, and credit card number. Bottom line? It’s smart to avoid any ads seeking to capitalize on the coronavirus. Tips for recognizing and trying to avoid phishing emailsHere are some ways to recognize and avoid coronavirus-themed phishing emails. Phishing email messages usually try to lure you into clicking on a link or providing personal information that can be used to commit fraud or identity theft. Here’s some tips to avoid getting tricked.
Excerpts taken from Norton Lifelock article here - Read Full Article Protect Your Company Against RansomwareRansomware attacks have been increasing over the last few years and are one of the leading causes of data loss for companies.
There are few steps that you can perform to help protect your company and your company data from ransomware attacks.
If you feel that you could use help with these steps please contact us - [email protected] Scam of the Week: Black Friday & Cyber Monday Alert
"With more people than ever poised to partake in this year’s November shopping frenzy, attackers will capitalize by using the brand names of leading e-tailers to exploit users looking for Black Friday deals and coupons by creating fake mobile apps and landing pages to fool consumers into downloading malware, using compromised sites, or giving up their login credentials and credit card information." "It's Holiday Season for the bad guys too! But not the way you might think. They go into scam-overdrive mode. Black Friday and Cyber Monday are the busiest on-line shopping days and they are out to get rich with your money. So what to look out for?
This alert is also at the KnowBe4 blog, and has additional resource links: https://blog.knowbe4.com/scam-of-the-week-black-friday-cyber-monday-alert Scam of the Week: SharePoint Phishing Attack on Office 365 Users
This latest attack uses several familiar aspects of O365 to lull potential victims into an assumption everything is above board. Be on alert! The bad guys have a new way of stealing your login credentials. They target you by sending you an invite via email to open a SharePoint document. The link takes you to an actual SharePoint page where you will see a OneDrive prompt. The prompt will have an “Access Document” link in it- don’t click this link! This link is malicious and will take you to a fake Office 365 login screen. Any credentials you enter here will be sent to the bad guys. Don't be tricked. Whenever you're submitting login credentials to any site, make sure to check the URL of the page for accuracy. Also, remember to always hover over links to see where they are taking you. Remember, Think Before You Click. Twitter's 330 million users are being urged to change their passwords after some were exposed in plain text on its internal network.
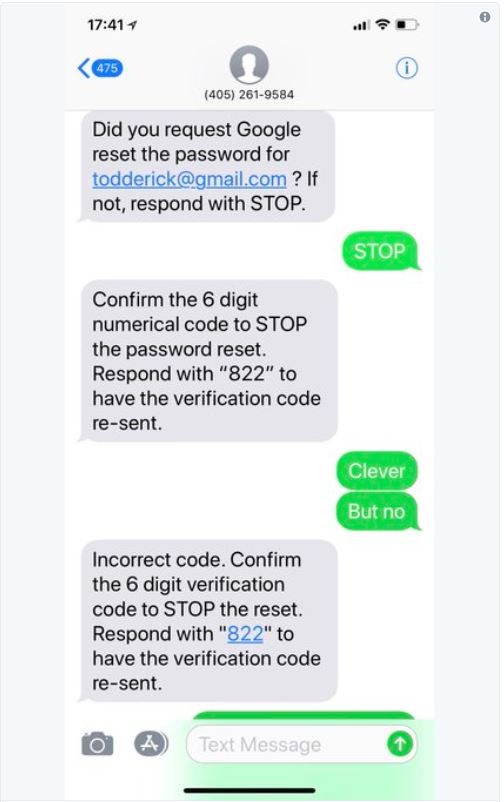
An error in the way the passwords were handled meant some were stored in easily readable form, said Twitter. The passwords should have been put through a procedure called "hashing" making them very difficult to read. Security experts said the way Twitter handled the potential breach was "encouraging". See whole story here - http://www.bbc.com/news/business-43995168 Twitter user @_thp shared a recent phishing scam that they received; and it’s so fiendishly clever that it’s gone viral. They wrote: "This is the most clever phishing scam I've ever encountered and for a second it almost got me." Now, that is perhaps a bit exagerated, but you have to admit it's something a lot of people will likely fall for,
See full story link below picture Please be aware of an email phishing scam that has started in the last week.
Companies are experiencing a wave of phishing scams that target employee paychecks. Here is the scenario: 1. An employee receives from a company email account e-mail that mimics a familiar and trusted company service or resource, such as an e-signature request or a request to complete a survey. 2. The e-mail asks the employee to click a link, access a website, or answer a few questions. 3. Then it directs the employee to “confirm” his or her identity by providing his or her complete log-in credentials. Skeptical employees who question the request via reply e-mail receive a prompt response purporting to verify that the employee should complete the steps contained in the link. 4. The threat actors then use the employee’s log-in credentials to access payroll portals, reroute direct deposits to other accounts, and wreak other havoc upon the employer’s network. In some versions of the scam, hackers access employee e-mails to request a password change from the employer’s payroll service and then use the new log-in credentials to change direct deposit instructions." Employers may want to immediately take the following precautions to avoid security breaches as a result of these phishing scams: • Alert your workforce to this scam. • Direct employees to forward any suspicious requests to the information technology or human resources departments, rather than replying to the e-mail. • Instruct employees to refrain from supplying log-in credentials or personally identifying information in response to any e-mail. For more detailed information see this link - https://blog.knowbe4.com/scam-of-the-week-wave-of-payroll-direct-deposit-phishing-attacks |
AuthorSr. Consultant - IndyTek Consulting Archives
January 2024
Categories |

 RSS Feed
RSS Feed
